This article appears as part of a seven-part series on Disaster Recovery planning, regardless of institution size and systems in production. Each article will consist of an activity designed to encourage readers to update their own initial DR plan, or even create a new one.
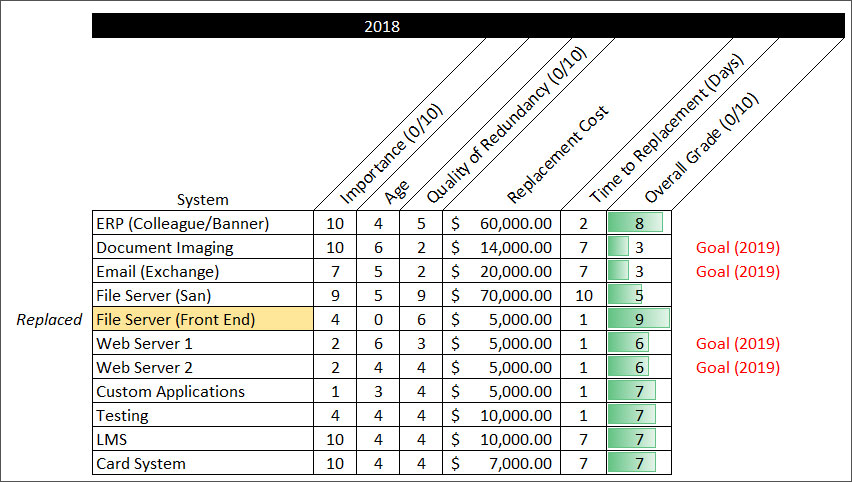
Our series on disaster recovery planning intends to challenge you to create an initial list of systems, ranked by criticality to the institution. The overall grade you assigned to those systems, subjective as it may be, is the correct number. Do not second guess your methodology, and do not re-rank systems. Because of your institutional knowledge, the background information that you possess about these systems is more relevant than any standard method you can find.
Now, we will move to addressing low-hanging fruit. By low-hanging fruit, consider this term to represent the least important system(s) in your list. Typically, an institution's least important systems are either homegrown applications or those procured by external vendors to serve a specific business function on campus (not necessarily those that have institutional-wide impact). Placing emphasis on these types of systems at this phase can help your team become comfortable with discussing the topic with stakeholders and serve as an easy introduction into how to justify cost and importance externally. Document the cost of redundancy, security, and performance in terms of the following metrics:
- Likelihood of failure
- Time to return of service given a light interruption
- Time to return of service in the event of a severe interruption
- A brief explanation of bare metal restoration (total loss)
Example: IT Ticketing System
- Likelihood of failure (3 out of 10).
- Time to return of service given a light interruption (2 hrs)
- Time to return of service in the event of a severe interruption (6 hrs)
- Time to return of service in case of total loss (1 day)
Explain under which circumstance each could happen. With this list in hand, you can now refer to the list to incite a real conversation with your peers. Important: Scaring others is never a good strategy. Make sure you ease everyone into the conversation by explaining the purpose of this exercise.
After you have completed the exercise with the first system in your list, move down the line to the next system, increasing priority.
You know your institution best, and you should make a judgement of how many of these systems you will address at the same time with your peers.
.png?width=110&height=116&name=Untitled%20design%20(25).png)